- Simply Cyber Newsletter
- Posts
- Simply Cyber Newsletter #165
Simply Cyber Newsletter #165
Crush Your Week Like a Cyber Pro with Simply Cyber!
AI-native CRM
“When I first opened Attio, I instantly got the feeling this was the next generation of CRM.”
— Margaret Shen, Head of GTM at Modal
Attio is the AI-native CRM for modern teams. With automatic enrichment, call intelligence, AI agents, flexible workflows and more, Attio works for any business and only takes minutes to set up.
Join industry leaders like Granola, Taskrabbit, Flatfile and more.
Start your work week off at full speed with expert analysis and actionable intel from top cybersecurity news stories. Share with your End Users, Peers, and Executives to support weekly security awareness with the Simply Cyber Newsletter!
FOR END USERS
Instagram denies breach amid claims of 17 million account data leak. Instagram says there was no new breach, but a bug allowed attackers to trigger mass password reset emails, causing panic. The leaked data appears to be old, compiled from past scraping incidents. The real risk now is phishing and scam messages that use this data to trick users.
What you need to know: Educate your end users about how attackers exploit fear and urgency, especially through password reset emails, account warnings, or messages claiming suspicious activity. Reinforce that unexpected reset emails do not mean an account is compromised and should not be clicked. Encourage users to access accounts only through apps or websites they already trust and use, not links in emails or texts.
Make it clear that reporting suspicious messages is always the right action, even if the email looks professional or appears to come from Instagram, Meta, or another trusted brand. Normalize reporting and remove the fear of embarrassment. Many users hesitate to report because they think they should have known better. Reporting helps protect everyone, not just the individual, and early reports can stop wider attacks.
FOR PEERS
n8n Supply Chain Attack Abuses Community Nodes to Steal OAuth Tokens. Threat actors abused n8n community nodes on npm to steal OAuth tokens by publishing malicious integrations that looked legitimate. Once installed, the nodes decrypted stored credentials using n8n’s master key and exfiltrated them. This highlights how workflow automation platforms have become high-value credential hubs and prime supply chain targets.
What you need to know: Share this story with your peers and have conversations about how workflow automation tools quietly concentrate risk. Last week we talked about automation platforms becoming high value targets because of the access they hold. This incident shows that shift becoming operational. n8n community nodes run with full access to environment variables, filesystems, outbound networking, and decrypted credentials, effectively making them privileged code. A single malicious package can expose OAuth tokens, API keys, and integrations across multiple systems at once. Use this as a prompt to review whether community packages are allowed, how integrations are vetted, and whether automation platforms are treated as tier zero assets. This is also an opportunity to align DevOps, security, and platform teams on ownership and guardrails for automation tooling, rather than assuming it is low risk glue code.
FOR EXECUTIVES
Exclusive: Beijing tells Chinese firms to stop using US and Israeli cybersecurity software, sources say. China has ordered domestic companies to stop using U.S. and Israeli cybersecurity software, citing national security concerns. The move signals that security tools themselves are now viewed as strategic infrastructure and potential geopolitical leverage points, not neutral defensive technology.
What you need to know: Share this story with your executives and frame it as a signal about how cybersecurity tools are increasingly viewed as strategic infrastructure, not neutral software. China’s move underscores a broader shift where security platforms themselves are treated as potential intelligence exposure, supply chain leverage, or geopolitical risk. This is not limited to China or state actors. Regulatory pressure, trade restrictions, or national security policy could force organizations to change vendors with little notice. Use this as a prompt to discuss whether your security stack is overly concentrated, how quickly critical tools could be replaced, and whether leadership visibility exists into these dependencies. This is about operational resilience and strategic optionality, not politics.

JOIN US EVERY WEEKDAY DAILY CYBER THREAT BRIEF
Gerald Auger, Ph.D. livestreams the Daily Cyber Threat Brief on Simply Cyber on weekdays at 8:00 AM EST.
Join the party with cybersecurity enthusiasts and professionals alike who enjoy learning about the latest in cybersecurity news and staying connected.
Meet #TeamSC in live chat and join the community! https://simplycyber.io/streams
NEW VIDEO SERIES: PRE VS JR VS SR GRC ANALYST
How GRC Professionals at Different Levels Answer the SAME Interview Question
Ever wondered what separates a junior analyst from a senior GRC leader? In this video, I put three cybersecurity professionals at different career stages to the test with the exact same challenging interview question:
"Tell me how you would handle a situation where a critical system fails a compliance audit, but the business wants to delay remediation for 6 months due to budget constraints."
Watch as I break down the differences between a junior analyst, mid-level GRC professional, and senior GRC leader's responses—and learn what hiring managers are really looking for at each level.
🎯 What You'll Learn:
Key differences in thinking between junior, mid, and senior GRC professionals
How to demonstrate business acumen in your answers
The importance of risk quantification and strategic thinking
Why documentation and stakeholder communication matter
How to position yourself as a trusted advisor
Check out the full video now on Simply Cyber Media Group: https://youtu.be/uzR28mmnXug
SIMPLY CYBER FIRESIDES WITH BRYSON BORT
In this episode of Simply Cyber Firesides, Gerald Auger, Ph.D. sits down with Bryson Bort, Cyber Unicorn and an accomplished business builders in the cybersecurity industry. Bryson is the Founder of SCYTHE, a next generation threat emulation platform, Founder of GRIMM, and Co Founder of the ICS Village, a nonprofit advancing awareness of critical infrastructure security. His career spans military service, entrepreneurship, policy advisory roles, and venture investment, giving him a rare perspective on building companies that matter.
🎯 In this Firesides conversation, Bryson will share:
What it really takes to start and scale cybersecurity companies
Lessons learned from founding multiple businesses and a nonprofit
Compensation models in startups including equity, cash, and risk tradeoffs
How to move from technical expertise into leadership and ownership
Why community building like ICS Village matters to the future of cyber
Advice for aspiring founders, operators, and early stage leaders
Bryson also brings experience as a former U.S. Army Officer, a board member supporting cyber education, and a trusted voice in national security and critical infrastructure discussions. This session is designed to be open, practical, and interactive.
💬 Join live and bring your questions. This is your opportunity to ask directly about startups, consulting, nonprofits, funding, career risk, and what Bryson wishes he knew when he started.
Register to attend now and meet us on Simply Cyber this Thursday: https://luma.com/jyxdzcim
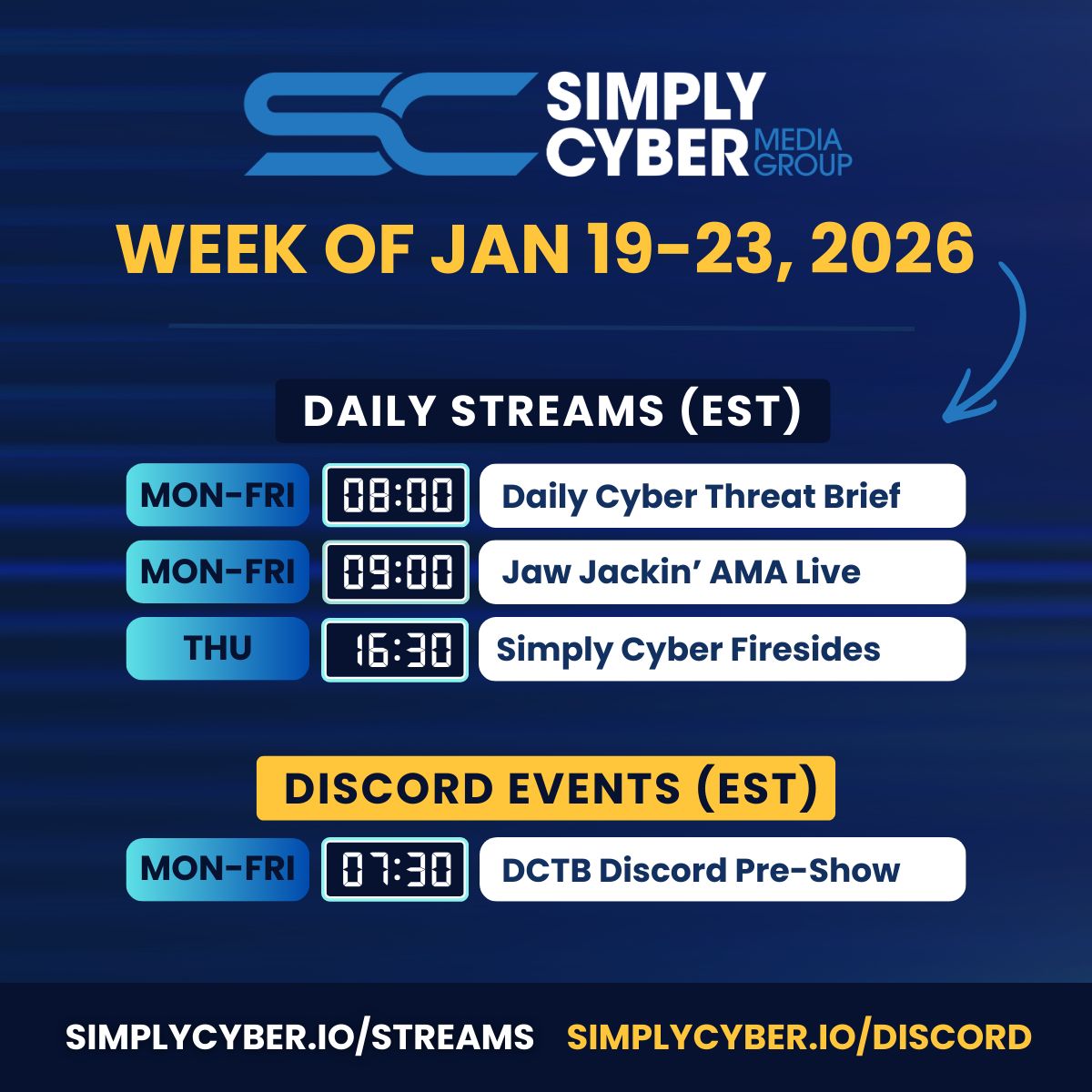
SC MEDIA GROUP WEEKLY EVENTS SCHEDULE
Join us for learning and networking: simplycyber.io/streams & simplycyber.io/discord
SC ACADEMY WORKSHOP AMPLIFY YOUR CYBER CAREER
In cybersecurity, your skills matter, AND so does your visibility.
The people getting promoted, landing speaking gigs, and fielding recruiter calls aren't just good at their jobs. They have a brand.
This 4-hour live workshop gets you from "I should probably do this" to "my channel is live and I have a plan."
Here's what you're walking away with:
Your YouTube channel launched and branded
Your first video strategy defined (no guessing what to create)
A thumbnail that actually gets clicks
The confidence to hit record
Who this is for: Cybersecurity professionals ready to be visible, build authority, and open doors.
Whether you're looking to land your next role, attract consulting clients, or position yourself as an expert, personal branding is how you get there.
Why YouTube? It's where hiring managers, recruiters, and conference organizers are looking. It's proof you know your stuff. And it builds your network faster than anything else.
I've built Simply Cyber from zero to 260K+ YouTube subscribers and a thriving community. YouTube changed my career trajectory completely.
This workshop shows you exactly how to start yours. This is live, hands-on, and action-packed. No fluff. No theory. Just practical steps to get your brand launched today.
Limited to 100 participants so everyone gets attention and leaves with results.
Ready to amplify your career? Let's build your brand.
Live Workshop Fee only $99 - Fee Waived - attend now for FREE!
Register today via Zoom: https://us06web.zoom.us/webinar/register/WN_R4r571WyQ8yvuzSwV14tzw#/registration
SIMPLY CYBER MONTHLY EVENTS SCHEDULE
Want to know what’s happening at Simply Cyber at any given time?
Head over to the SC Monthly Events Calendar to register for new and upcoming events for the month - don’t forget to subscribe! lu.ma/simplycyber
SC ACADEMY THE PLACE FOR CYBER CAREERS
At Simply Cyber Academy, we specialize in making GRC and Cybersecurity Careers a reality. Empower your career by learning real in-demand skills from cyber experts and the theory behind those skills with Simply Cyber Academy.
The popular GRC Analyst Master Class is a must for kickstarting your GRC Cybersecurity career. In addition, we have new courses covering various areas of focus in cyber available to help you advance in your career.
Check out the NEW FREE courses available in the academy and our new blog!
LET’S CONNECT
Stay current on trending topics, tips, events and resources in cybersecurity, connect with Simply Cyber on socials for new content.
As always, please send me feedback. Which tip above is your favorite? What do you want more or less of? Other suggestions? Please let me know. Just send a DM on X with #actionableintel in the subject so I can find it.
Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Find more about what’s happening this week in the Simply Cyber community, below. Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Thank you and see you again next week, #TeamSC!
Gerry