- Simply Cyber Newsletter
- Posts
- Simply Cyber Newsletter #162 🎆
Simply Cyber Newsletter #162 🎆
Crush Your Week Like a Cyber Pro with Simply Cyber!
Start your work week off at full speed with expert analysis and actionable intel from top cybersecurity news stories. Share with your End Users, Peers, and Executives to support weekly security awareness with the Simply Cyber Newsletter!
FOR END USERS
86% Surge in Fake Delivery Websites Hits Shoppers During Holiday Rush. Cybercriminals are creating fake delivery websites and sending phishing texts and emails that appear to come from postal and shipping companies. During the holiday rush, these scams use delayed package warnings to trick people into clicking links and entering personal or financial information..
What you need to know: Cybercriminals are creating convincing fake delivery messages that appear to be shipping alerts from legitimate carriers. These texts and emails often claim a package is either delayed or requires payment and include links that lead to malicious websites designed to steal personal or financial information.
Although the peak holiday shopping season has largely concluded, these scams remain effective during the weeks that follow. People are still tracking late packages, exchanging gifts, processing returns, and waiting for replacements. That uncertainty creates new opportunities for scammers to exploit people's sense of urgency and curiosity.
If you receive a delivery message, do not click the link in the text or email. Instead, go directly to the retailer or carrier website and enter the tracking number yourself. Be cautious of messages that ask for fees or personal information, and report suspicious alerts to the carrier rather than responding to them.
FOR PEERS
WebRAT malware spread via fake vulnerability exploits on GitHub. Threat actors are distributing the WebRAT backdoor through fake GitHub repositories posing as proof-of-concept exploits, luring researchers and developers into executing a dropper that disables Defender, elevates privileges, and installs an info-stealing backdoor.
What you need to know: Share this story with your peers and have conversations about how your organization manages the risk of downloading code from GitHub, especially proof-of-concept exploit repositories. This incident highlights how threat actors are targeting security researchers, developers, and IT staff by disguising malware as research tools.
Use this as an opportunity to review internal expectations for testing exploits, scripts, and security research tools. Discuss whether teams are using isolated environments, disposable virtual machines, or dedicated lab systems before running untrusted code. Reinforce that AI-written repository text, security-themed filenames, or mentions of mitigations do not necessarily indicate a repository's legitimacy.
Encourage teams to verify sources, avoid running unknown binaries, and treat public code as untrusted by default. Curiosity and research are valuable, but safe handling practices are what prevent a lab test from becoming an enterprise incident.
FOR EXECUTIVES
Trump signs defense bill allocating millions for Cyber Command, mandating Pentagon phone security. The 2026 National Defense Authorization Act preserves the shared leadership structure between U.S. Cyber Command and the NSA, funds expanded cyber operations, and directs the Defense Department to improve secure communications and provide senior leaders with mobile devices that include stronger cybersecurity protections.
What you need to know: Share this story with your executives and have conversations about whether your organization has a secure, approved channel for leadership communications and whether it is actually being used in practice. This bill reinforces that secure communication at the senior level is now a national security priority, not a technical detail. Use this moment to review how sensitive discussions are handled during incidents, confirm that consumer messaging tools are not being used for operational decisions, and ensure accountability for secure communication is clearly assigned. The goal is simple: executive behavior should strengthen resilience, not introduce avoidable risk.

JOIN US EVERY WEEKDAY DAILY CYBER THREAT BRIEF
Gerald Auger, Ph.D. livestreams the Daily Cyber Threat Brief on Simply Cyber on weekdays at 8:00 AM EST.
It’s a party full of cybersecurity enthusiasts and professionals of all levels who enjoy learning about the latest in cybersecurity news and staying connected.
Meet #TeamSC in live chat and join the community! https://simplycyber.io/streams
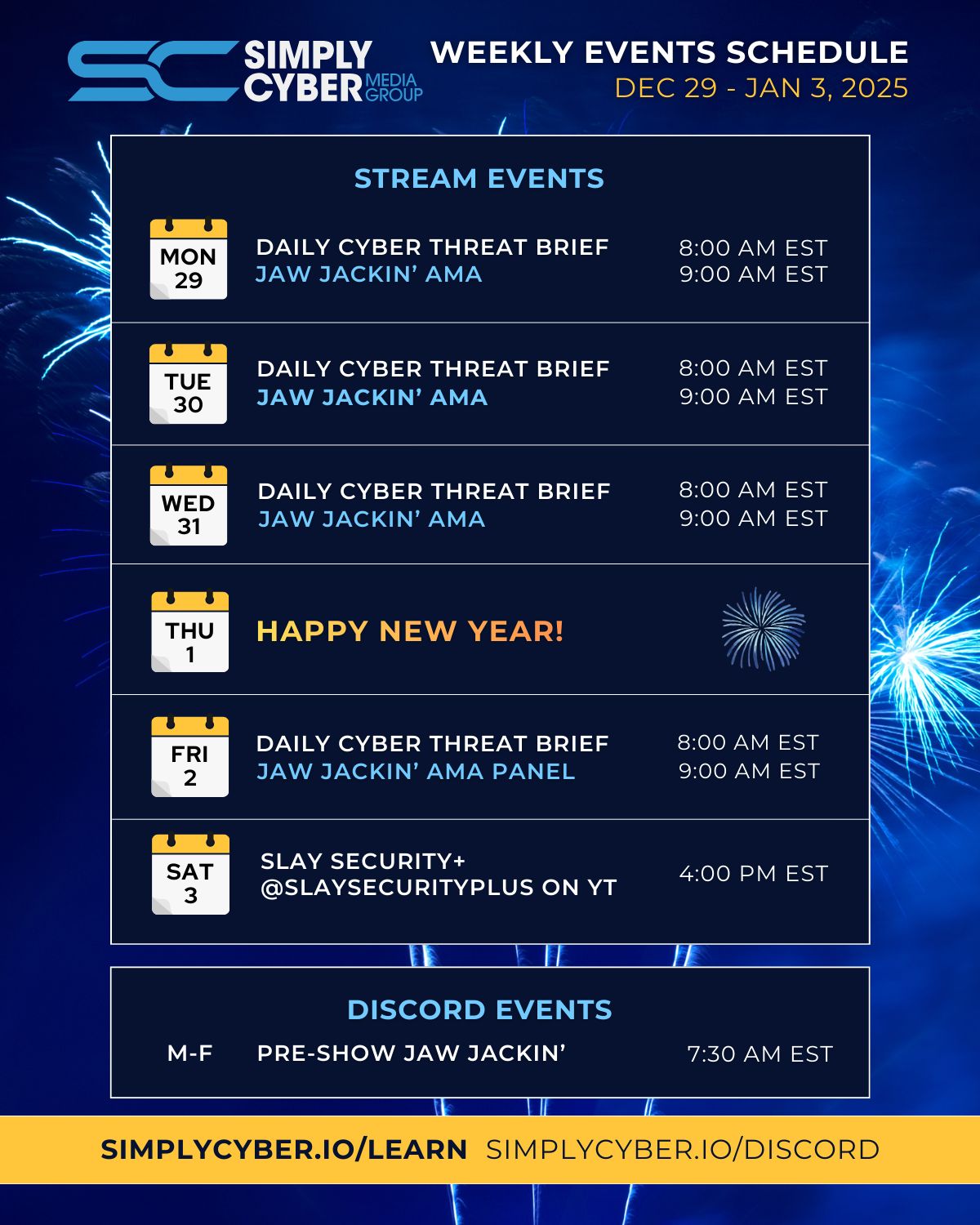
SC MEDIA GROUP WEEKLY EVENTS SCHEDULE 🎄
Join us for learning and networking: simplycyber.io/learn & simplycyber.io/discord
SC ACADEMY THE PLACE FOR CYBER CAREERS
At Simply Cyber Academy, we specialize in making GRC and Cybersecurity Careers a reality. Empower your career by learning real in-demand skills from cyber experts and the theory behind those skills with Simply Cyber Academy.
The popular GRC Analyst Master Class is a must for kickstarting your GRC Cybersecurity career. In addition, we have new courses covering various areas of focus in cyber available to help you advance in your career.
Check out the NEW FREE courses available in the academy and our new blog!
LET’S CONNECT
Stay current on trending topics, tips, events and resources in cybersecurity, connect with Simply Cyber on socials for new content.
As always, please send me feedback. Which tip above is your favorite? What do you want more or less of? Other suggestions? Please let me know. Just send a DM on X with #actionableintel in the subject so I can find it.
Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Find more about what’s happening this week in the Simply Cyber community, below. Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Thank you and see you again next week, #TeamSC!
Gerry