- Simply Cyber Newsletter
- Posts
- Simply Cyber Newsletter #153
Simply Cyber Newsletter #153
Crush Your Week Like a Cyber Pro with Simply Cyber!
Start your work week off at full speed with expert analysis and actionable intel from top cybersecurity news stories. Share with your End Users, Peers, and Executives to support weekly security awareness with the Simply Cyber Newsletter!
FOR END USERS
Researchers track surge in high-level Smishing Triad activity. A massive global scam operation called Smishing Triad is sending highly convincing fake text messages pretending to be toll services, USPS, banks, and even tax agencies. These fake links lead to lookalike websites designed to steal personal and financial information in seconds.
What you need to know: Educate your end users about the growing wave of fraudulent text messages pretending to be legitimate services like the Postal Service, toll agencies, banks, or even tax departments. These messages often claim there is a failed delivery, unpaid balance, or urgent account issue and include a link that looks real at a quick glance. That link is the trap. The scammers behind this campaign have built an industrial-scale system that registers tens of thousands of fake websites every month and throws them away within days, making them almost impossible to block fast enough. The safest response is simple: never tap a link in an unexpected text. Instead, go to the official website or app yourself. If it feels urgent, that is intentional pressure. Slow down, verify, and report suspicious messages to your security or IT team immediately.
Take a screenshot of what this attack looks like so your end users can visually recognize it. Encourage them to educate friends and family, especially those who pay tolls, shop online, or rely on package delivery, because this threat spreads fastest when people assume they are too smart to fall for it.
FOR PEERS
F5 BREACH EXPOSES 262,000 BIG-IP SYSTEMS WORLDWIDE. A nation-state breach at F5 resulted in source code and undisclosed vulnerability data being stolen, and over 260,000 BIG-IP devices remain exposed online. Any unpatched F5 gear is now operating under the assumption of adversarial insider-level knowledge.
What you need to know: Share this story with your peers and have conversations about what your organization is doing to immediately verify all F5 BIG-IP, BIG-IQ, and F5OS appliances are identified, fully patched, and not directly exposed to the open internet. Assume adversaries now have development level understanding of how these systems operate. If your organization does not use F5, use this as a stress test scenario and honestly ask how quickly you could locate, isolate, and harden any internet-facing infrastructure if your vendor suffered a similar breach. Review credential hygiene, ensure EDR coverage exists on the access paths into these devices, and confirm that patching is not waiting on a maintenance window. It is important for end users to understand that they are truly the last line of defense in some situations.
FOR EXECUTIVES
A single DNS race condition brought Amazon's cloud empire to its knees. A race condition in AWS DynamoDB's automated DNS system triggered a cascading outage across EC2, Lamda, and other core cloud services, disrupting major brands and government services for hours. The failure was systemic and interconnected, proving cloud dependence has operational, financial, and reputational risk at board level.
What you need to know: Have a conversation with your senior leaders about whether your business would stay operational if a major service you depend on failed without warning. The AWS incident is a reminder, not the only scenario. The same risk applies if your payment processor stalls, your internet carrier goes offline, your authentication provider locks users out, or your logistics platform halts. These are not rare events. They are happening more frequently and faster than most businesses detect. This is no longer about prevention. It is about resilience. The key question is not whether failure will occur but whether the business continues functioning when it does.
If the conversation turns to this topic, be prepared to ask: Do we have even one critical dependency that, if unavailable for twelve hours, would pause revenue, stop access, or break customer trust immediately?
Find out why 100K+ engineers read The Code twice a week
Staying behind on tech trends can be a career killer.
But let’s face it, no one has hours to spare every week trying to stay updated.
That’s why over 100,000 engineers at companies like Google, Meta, and Apple read The Code twice a week.
Here’s why it works:
No fluff, just signal – Learn the most important tech news delivered in just two short emails.
Supercharge your skills – Get access to top research papers and resources that give you an edge in the industry.
See the future first – Discover what’s next before it hits the mainstream, so you can lead, not follow.

SIMPLY CYBER MEDIA GROUP PODCAST HIGHLIGHT
Cyber Burnout, AI Takeover & the Future of Simply Cyber with Gerald Auger, Ph.D.
Today on 2 Cyber Chicks, we’re joined by the one and only Dr. Gerald Auger, the creator of Simply Cyber, educator, and community builder who’s helped thousands break into and thrive in cybersecurity.
In this episode, we get real about: 💡 Burnout in Cybersecurity — how to spot it, manage it, and bounce back stronger 🌐 Reshaping Simply Cyber — Gerald’s vision for keeping the platform community-driven and impactful 🤖 The Future of AI in Cyber — opportunities, risks, and how AI will shape defenders and attackers alike 🚀 Breaking Into Cyber — Gerald’s best advice for anyone just starting out Whether you’re a cyber pro, career changer, or just curious about the human side of security, this conversation is full of insights, laughs, and practical takeaways.
👉 Join us: https://youtu.be/OqW4f6cThfY
Visit https://www.youtube.com/@SimplyCyber/podcasts to catch up on all of the podcasts available on Simply Cyber Media Group!
SIMPLY CYBER FIRESIDES TYLER RAMSBEY
From Hacker to Founder with Tyler Ramsbey - hacker, sr. pentester, community founder at Hack Smarter, mentor, and now founder and Principal Security Consultant at Kairos Sec.
Tyler recently made the bold leap from a desirable full-time pentesting role to launching his own cybersecurity company - and he’s pulling back the curtain on what that journey really looks like.
In this live conversation, we’ll cover: 💥 What it takes to start your own cyber company 🧠 Lessons learned from years in offensive security 💻 Insights into pentesting, hacking, and content creation 🚀 The risks, rewards, and mindset shifts of becoming a founder
Plus, live audience Q&A throughout the show!
Bring your questions and join the chat as we explore how one hacker turned his passion into a business built on cybersecurity excellence. 🔒
Don’t miss it - this is where cyber careers, leadership, and entrepreneurship collide: https://youtube.com/live/_HaIhcA1iQs
SIMPLY CYBER CON 2025
When: Sunday, Nov. 2nd & Monday, Nov. 3rd
Simply Cyber Con is almost here!
Head over to the website to learn more about conference registration and training day options.
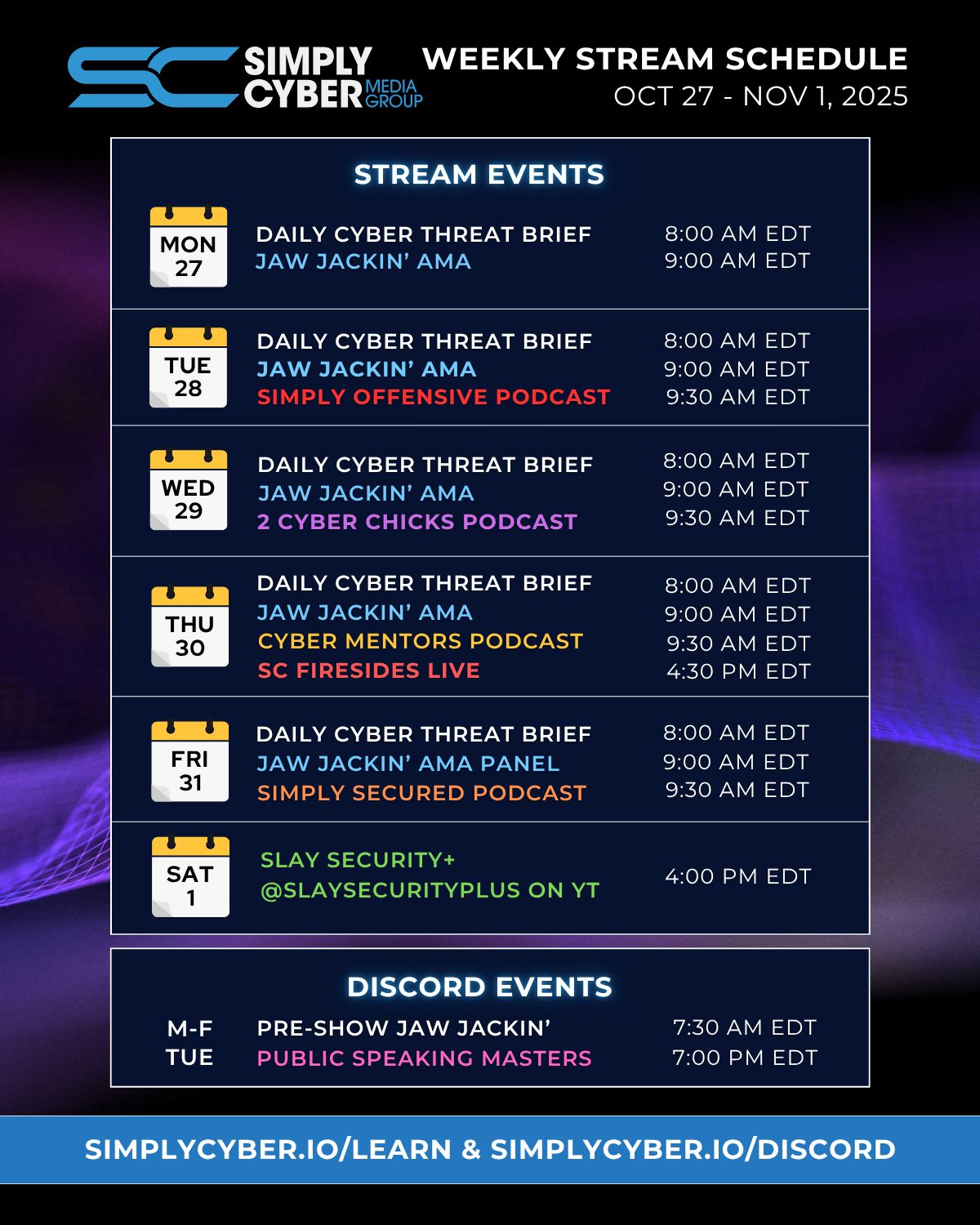
SC MEDIA GROUP WEEKLY EVENTS SCHEDULE
Join us for learning and networking: simplycyber.io/learn & simplycyber.io/discord
SC ACADEMY THE PLACE FOR CYBER CAREERS
At Simply Cyber Academy, we specialize in making GRC and Cybersecurity Careers a reality. Empower your career by learning real in-demand skills from cyber experts and the theory behind those skills with Simply Cyber Academy.
The popular GRC Analyst Master Class is a must for kickstarting your GRC Cybersecurity career. In addition, we have new courses covering various areas of focus in cyber available to help you advance in your career.
Check out the NEW FREE courses available in the academy and our new blog!
LET’S CONNECT
Stay current on trending topics, tips, events and resources in cybersecurity, connect with Simply Cyber on socials for new content.
As always, please send me feedback. Which tip above is your favorite? What do you want more or less of? Other suggestions? Please let me know. Just send a DM on X with #actionableintel in the subject so I can find it.
Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Find more about what’s happening this week in the Simply Cyber community, below. Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Thank you and see you again next week, #TeamSC!
Gerry