- Simply Cyber Newsletter
- Posts
- Simply Cyber Newsletter #150
Simply Cyber Newsletter #150
Crush Your Week Like a Cyber Pro with Simply Cyber!
Start your work week off at full speed with expert analysis and actionable intel from top cybersecurity news stories. Share with your End Users, Peers, and Executives to support weekly security awareness with the Simply Cyber Newsletter!
FOR END USERS
Fake Microsoft Teams installers push Oyster malware via malvertising. AThreat actors are using SEO poisoning and fake ads to push a malicious Microsoft Teams installer that infects Windows devices with the Oyster backdoor. Because these fake links appear at the top of search results, not just in sponsored spots, users may mistake them for legitimate downloads from Microsoft.
What you need to know: Educate your end users to avoid downloading software directly from search results. Threat actors are using search engine tricks to make fake Microsoft Teams download sites appear at the very top of legitimate search pages. These sites look convincing, use familiar logos, and even have correctly named files, but they install malware instead of real software.
Remind employees that no matter how trusted a brand appears, the safest way to install tools like Teams is through official company channels or bookmarked links shared by IT. If they need software to do their job, they should submit a request or use the company’s approved software center. This ensures updates, licenses, and security checks are properly managed.
Attackers count on people taking shortcuts or assuming the first result is safe. Encourage everyone to pause before clicking, follow company guidance, and always verify before downloading or installing any software.
FOR PEERS
Nearly 50,000 Cisco firewalls vulnerable to actively exploited flaws. Tens of thousands of Cisco ASA and FTD firewalls remain unpatched against two actively exploited vulnerabilities that allow remote code execution and unauthorized VPN access. With no workarounds available, organizations should prioritize patching and restrict VPN web exposure immediately to reduce the risk of compromise.
What you need to know: "Share this story with your peers and have conversations about what your organization is doing to identify and patch Cisco ASA and FTD devices affected by CVE-2025-20333 and CVE-2025-20362. These vulnerabilities enable remote, unauthenticated code execution and VPN access, and they are being exploited in the wild.
It is important for end users to understand that they are truly the last line of defense in some situations, but infrastructure security starts with visibility and timely updates. Encourage teams to verify firmware versions, review VPN access logs, and restrict external management interfaces whenever possible.
Organizations should also reevaluate how they monitor for pre-exploitation scans, since early indicators were seen weeks before the attacks began. Patching and segmentation remain the most effective safeguards against these ongoing campaigns.
To hear more of my thoughts on this, also check out last Monday's stream (9/29) and go to the last story of the day before Jaw Jackin’.
FOR EXECUTIVES
Cybercriminals are trying to extort executives with data allegedly stolen through Oracle tool. A threat group possibly linked to the Clop ransomware gang is attempting to extort corporate executives by claiming to have stolen sensitive data from Oracle’s E-Business Suite. While the claims remain unverified, the campaign highlights how extortion tactics now target leadership directly, regardless of company size or industry.
What you need to know: Executives should be aware that extortion campaigns are increasingly targeting leadership, not just infrastructure. A recent operation attributed to a threat group potentially connected to Clop ransomware claims to have stolen data through Oracle’s E-Business Suite, a business platform used for finance and supply chain management. Whether or not the breach is real, the tactic is strategic—threat actors know that pressure on executives drives faster decisions and larger payouts.
Even if your organization does not use Oracle systems, the lesson applies broadly. Data extortion does not require direct compromise of your network; an attacker only needs convincing evidence to create fear and urgency. Executives should ensure their company’s incident response plans include protocols for extortion attempts, communication strategies, and external verification procedures before reacting to any threat.
If the conversation turns to this topic, be prepared to ask: 1. How do we validate claims before responding to extortion demands? 2. Who is authorized to communicate externally during such events? 3. Are our executives trained to recognize digital coercion tactics?

SIMPLY CYBER MEDIA GROUP PODCAST HIGHLIGHT
This Friday at 9:30 AM EDT on Simply Cyber Media Group
In this episode, James chats with Cristina Pawlica, a distinguished member of the Simply Cyber community with an extensive background in cybersecurity and military service. Cristina shares her unique journey from serving in the Air Force as a Force Support Officer to pursuing a career in cybersecurity.
She delves into crucial leadership lessons and discusses the significant role of cybersecurity in K-12 education institutions. The conversation touches on her active involvement in the 2010 Foundation, which supports Air Force Academy cadets, and her passion for volunteering and helping build cyber resilience.
This episode concludes with a rapid-fire segment, providing a fun glimpse into Christina's personal preferences and insights on cybersecurity.
Join us after the Daily Cyber Threat Brief this Friday! https://youtu.be/EqG9Ny7g84M
Visit https://www.youtube.com/@SimplyCyber/podcasts to catch up on all of the podcasts available on Simply Cyber Media Group!
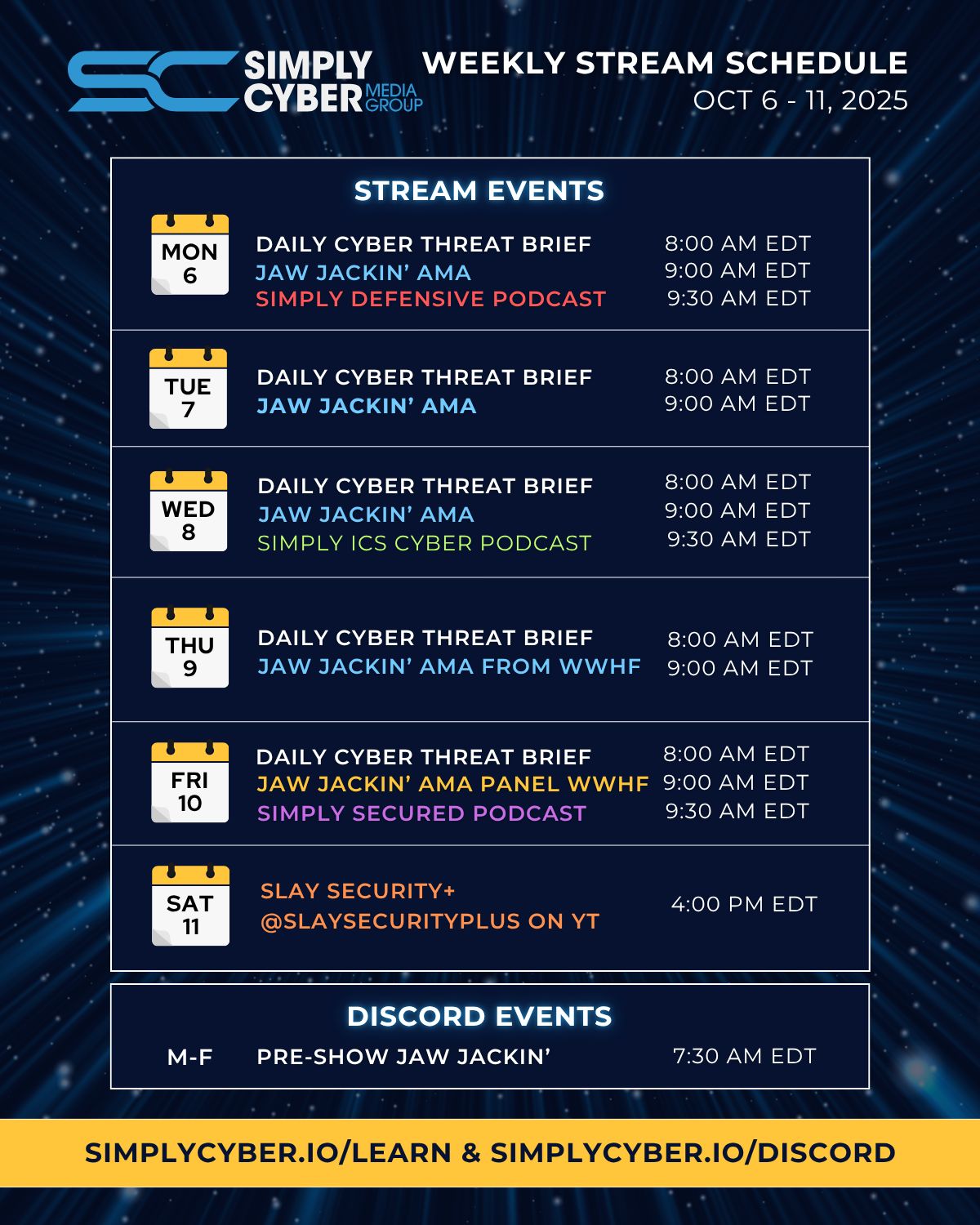
SC MEDIA GROUP WEEKLY EVENTS SCHEDULE
Join us for learning and networking: simplycyber.io/learn & simplycyber.io/discord
SIMPLY CYBER CON 2025
When: Sunday, Nov. 2nd & Monday, Nov. 3rd
We’re excited to share Simply Cyber Con is back for the third year in a row!
Registration is now available! Head over to the website to learn more about conference registration and training day options.
Don’t miss the opportunity to attend onsite training in-person with the amazing instructors on Nov. 2nd!
Stay tuned for updates! #simplycybercon
SC ACADEMY THE PLACE FOR CYBER CAREERS
At Simply Cyber Academy, we specialize in making GRC and Cybersecurity Careers a reality. Empower your career by learning real in-demand skills from cyber experts and the theory behind those skills with Simply Cyber Academy.
The popular GRC Analyst Master Class is a must for kickstarting your GRC Cybersecurity career. In addition, we have new courses covering various areas of focus in cyber available to help you advance in your career.
Check out the NEW FREE courses available in the academy and our new blog!
LET’S CONNECT
Stay current on trending topics, tips, events and resources in cybersecurity, connect with Simply Cyber on socials for new content.
As always, please send me feedback. Which tip above is your favorite? What do you want more or less of? Other suggestions? Please let me know. Just send a DM on X with #actionableintel in the subject so I can find it.
Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Find more about what’s happening this week in the Simply Cyber community, below. Join us on the Daily Cyber Threat Brief happening every weekday morning at 8 AM Eastern on YouTube and LinkedIn.
Thank you and see you again next week, #TeamSC!
Gerry